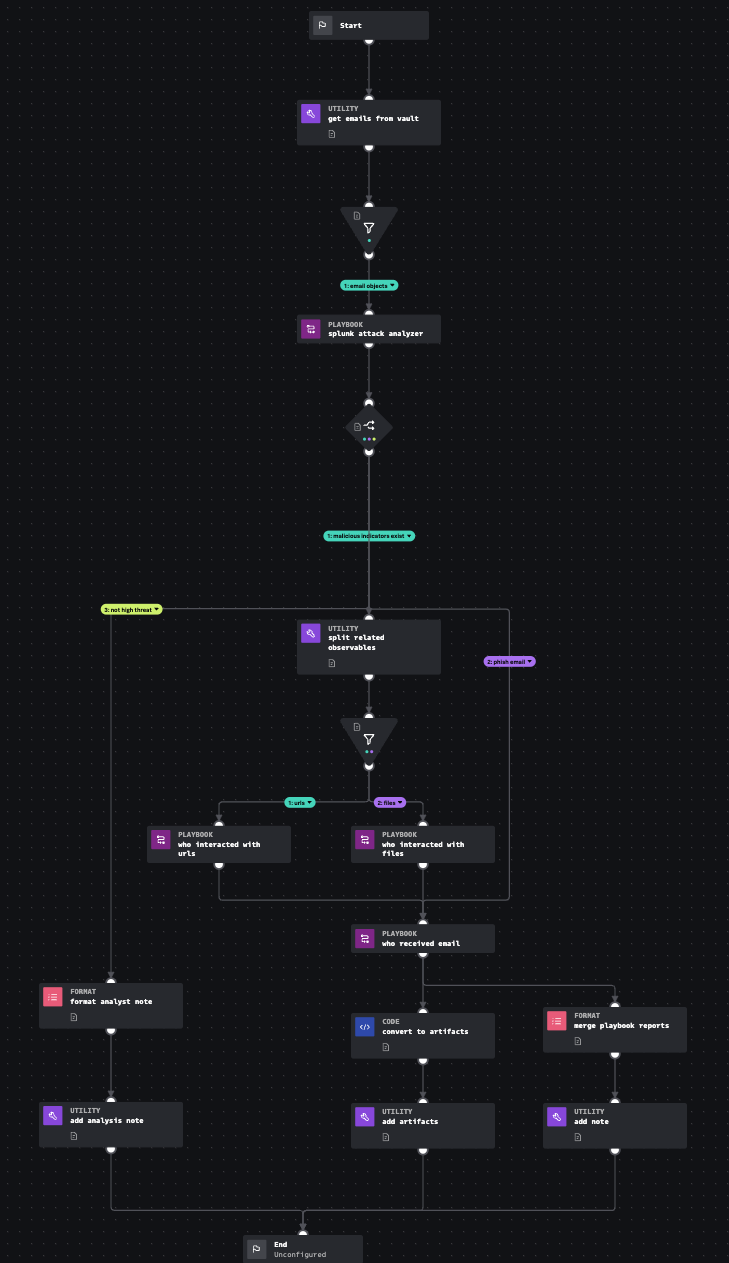
Playbook: Splunk Automated Email Investigation
Description
Leverages Splunk technologies to determine if a .eml or .msg file in the vault is malicious, whether or not it contained suspect URLs or Files, and who may have interacted with the IoCs (email, URLs, or Files).
How To Implement
Ensure the four input playbooks are loaded onto the system. The input playbooks are designed to be swappable within the same category (e.g., Message Activity Analysis) with minimal to no changes downstream.
Explore Playbook
Click the playbook screenshot to explore in more detail!
Reference
source | version: 1