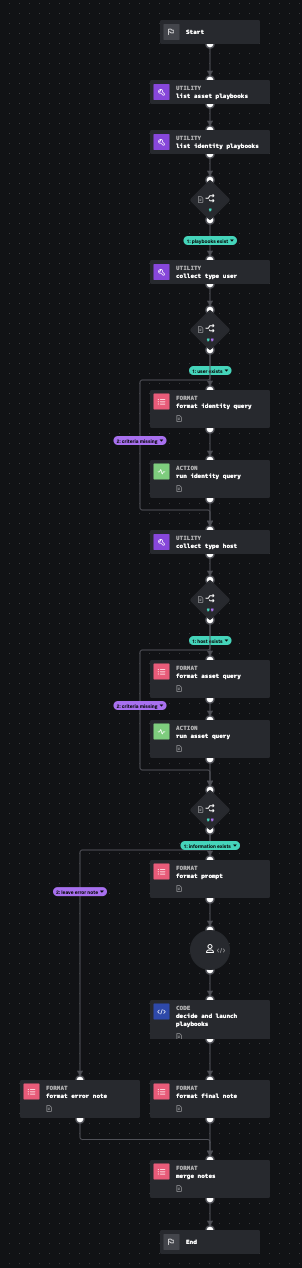
Playbook: Risk Notable Protect Assets and Users
Description
This playbook attempts to find assets and users from the notable event and match those with assets and identities from Splunk ES. If a match was found and the user has playbooks available to contain entities, the analyst decides which entities to disable or quarantine.
How To Implement
For detailed implementation see https://help.splunk.com/en/splunk-enterprise-security-8/security-content-update/how-to-use-splunk-security-content/5.8/use-splunk-soar-playbooks-and-workbooks-from-the-risk-notable-playbook-pack/get-started-with-the-risk-notable-playbook-pack-for-splunk-soar
Explore Playbook
Click the playbook screenshot to explore in more detail!
Reference
source | version: 1