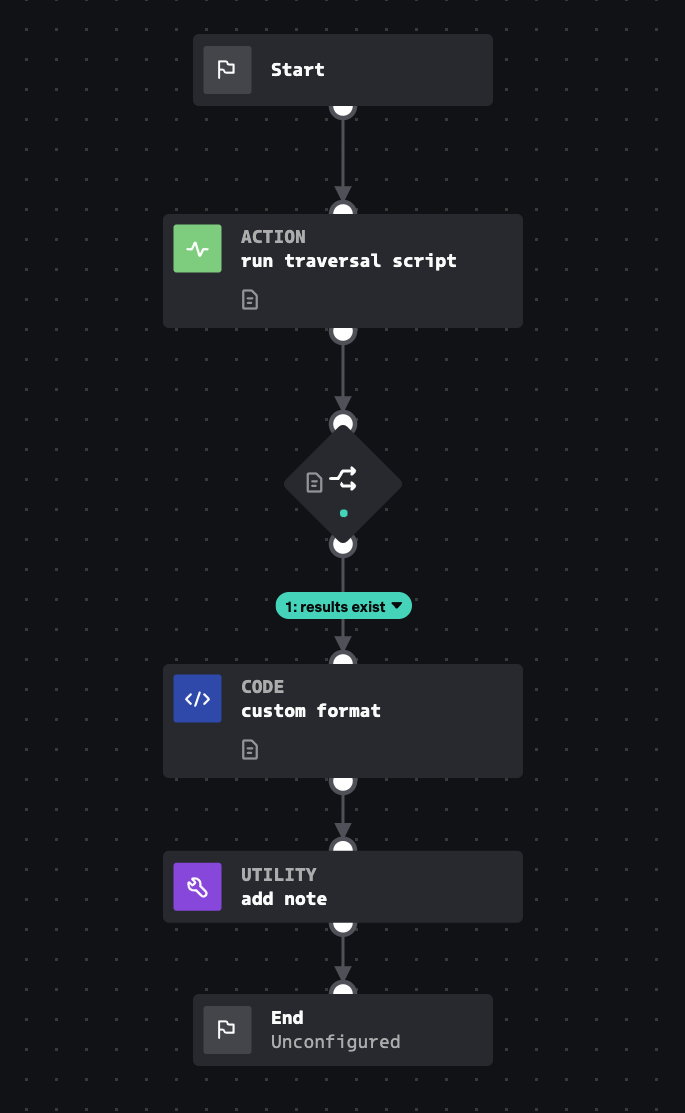
Playbook: Internal Host WinRM Log4j Investigate
Description
Published in response to CVE-2021-44228, this playbook uses WinRM to scan Windows endpoints for the presence of "jndilookup.class" in all .jar files. The presence of that string could indicate a log4j vulnerability.
Apps
How To Implement
The winrm asset requires Administrator access to scan the whole file system.
Explore Playbook
Click the playbook screenshot to explore in more detail!
Reference
source | version: 1