Playbook: CrowdStrike OAuth API Executable Denylisting
Description
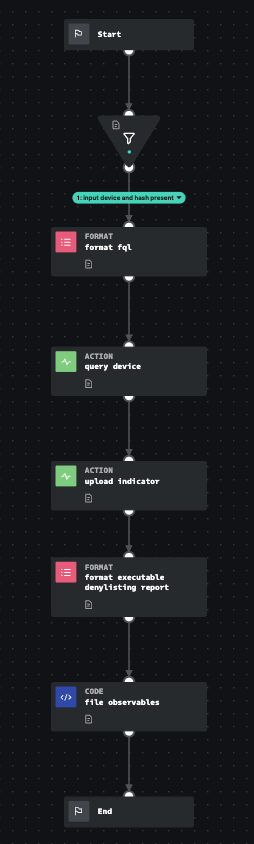
Accepts a hostname or device id as well as a file hash as input and add an indicator (IOC) for a device in Crowdstrike. We then generate an observable report as well as a Markdown formatted report. Both reports can be customized based on user preference.
Apps
How To Implement
This input playbook requires the CrowdStrike OAuth API connector to be configured. It is designed to work with an endpoint hostname or device id and create an indicator in CrowdStrike Falcon based on the malicious process hash value (preventing it from running on other endpoints) for use in automation playbooks.
Explore Playbook
Click the playbook screenshot to explore in more detail!
Required fields
-
device
-
file_hash
Reference
source | version: 1