Playbook: Crowdstrike Malware Triage
Description
This playbook is used to enrich and respond to a CrowdStrike Falcon detection involving a potentially malicious executable on an endpoint. Check for previous sightings of the same executable, hunt across other endpoints for the file, gather details about all processes associated with the file, and collect all the gathered information into a prompt for an analyst to review. Based on the analyst's choice, the file can be added to the custom indicators list in CrowdStrike with a detection policy of "detect" or "none", and the endpoint can be optionally quarantined from the network.
Apps
How To Implement
This playbook uses the Crowdstrike OAuth app. Change the target user of the prompt from admin to the appropriate user or role.
Explore Playbook
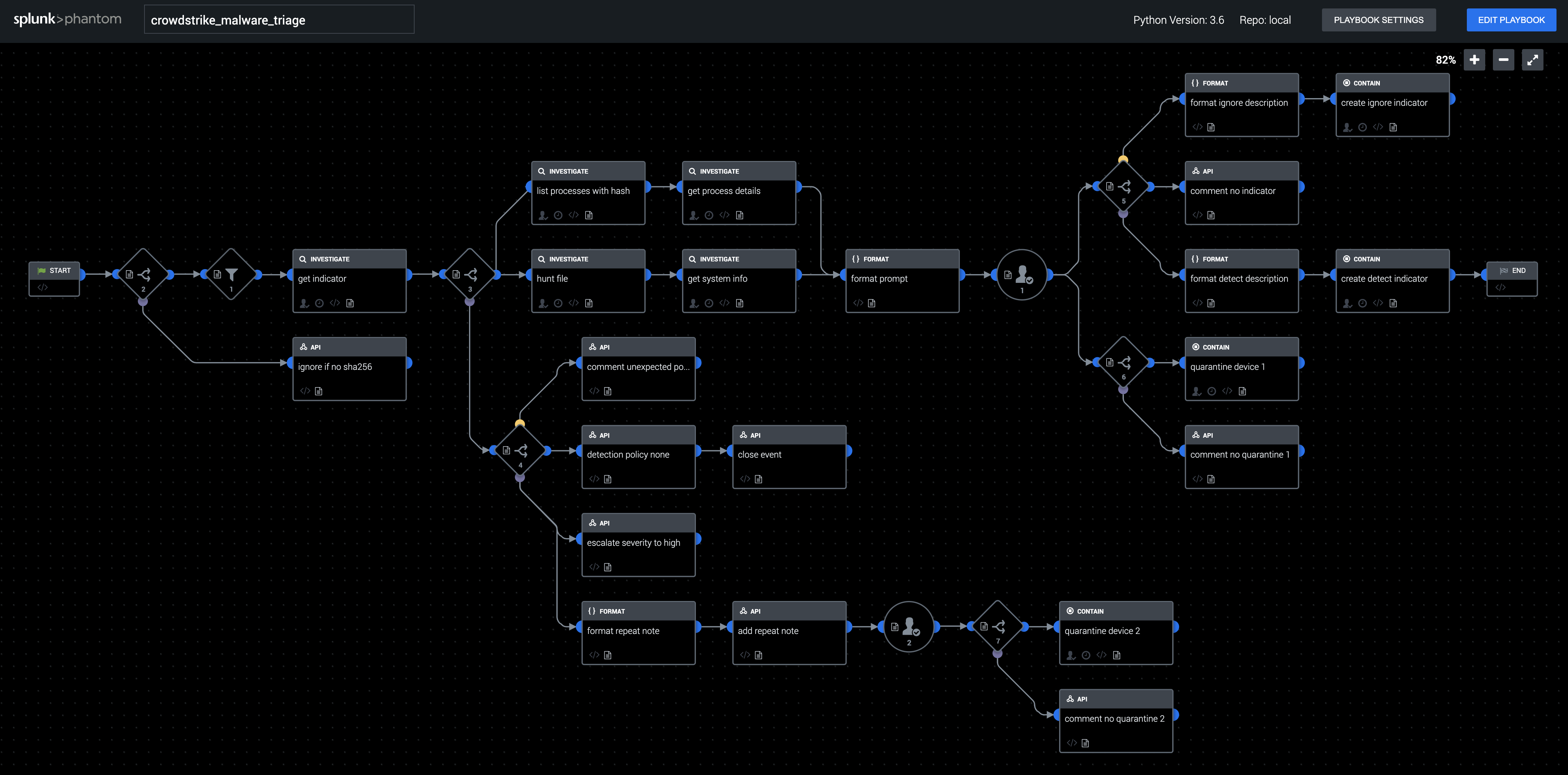
Required fields
-
filePath
-
destinationAddress
Reference
source | version: 1
